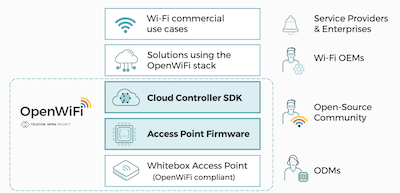
As Virtual Reality (VR) expands beyond home entertainment into business and healthcare sectors, ensuring a robust WiFi connection becomes increasingly critical. Whether it's for training simulations in a corporate setting or for advanced medical procedures, a lag-free VR experience is essential. This is where a WiFi Scanner becomes an invaluable tool for optimizing your network.